Architecture Overview
AVA is deployed as a private, single-tenant application within your Azure environment. This architecture ensures your data never leaves your tenant while providing enterprise-grade AI capabilities through a secure, identity-based access model.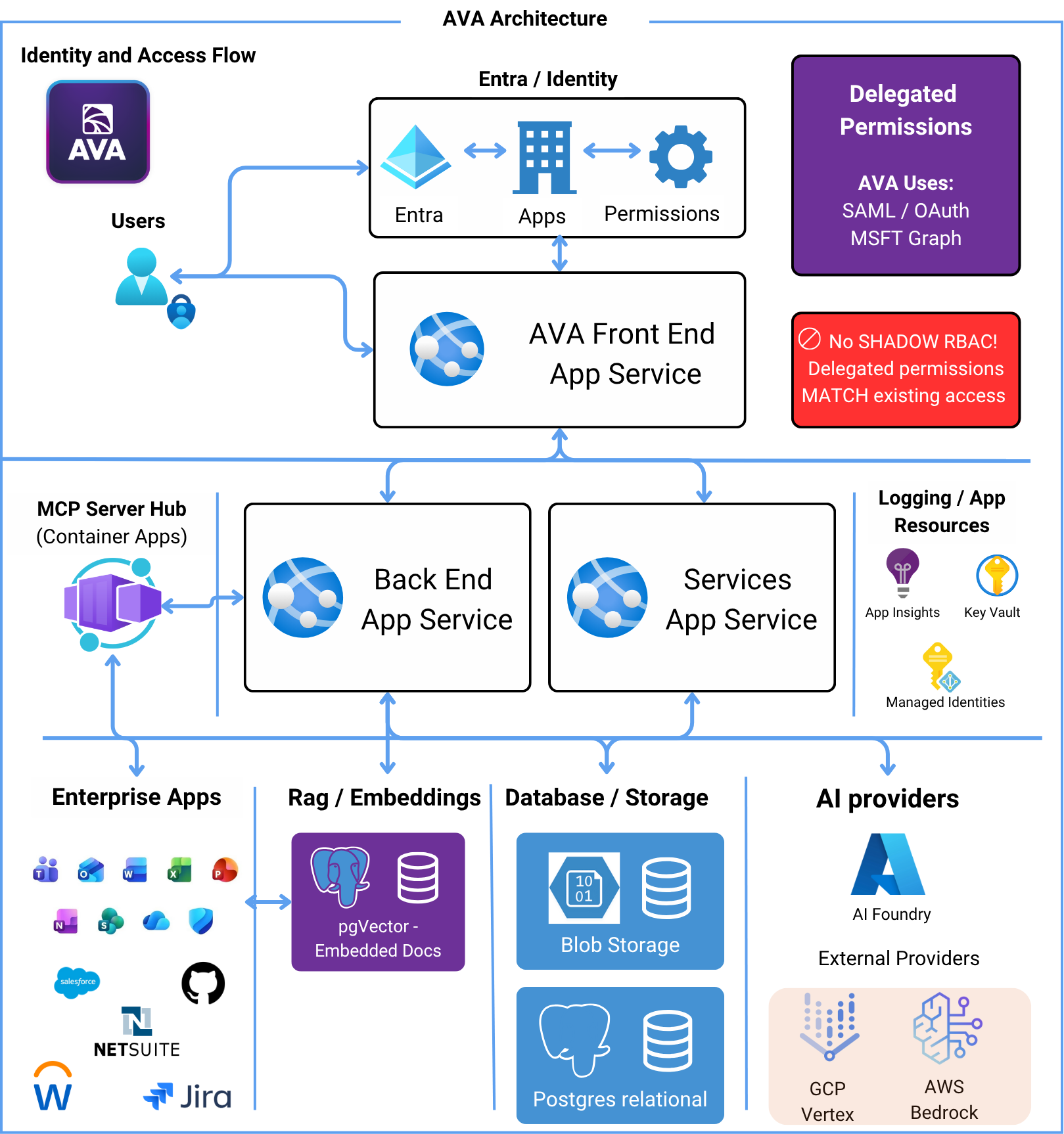
Identity and Access Flow
The foundation of AVA’s security model is delegated permissions through Microsoft Entra ID:User Authentication
Users sign in to AVA using their Microsoft work account (same credentials used for Office 365)
Entra ID Verification
Microsoft Entra ID authenticates the user and establishes their identity and permissions
Delegated Access
AVA operates with the user’s permissions—it can only access what the authenticated user can access
System Architecture
Frontend Layer
AVA Front End App Service (Azure App Service)- React-based web application
- Handles user interface and interactions
- Communicates with backend via secure APIs
- Session management and state
Backend Layer
Two primary backend services running as Azure Container Apps:- Back End App Service
- Services App Service
Core orchestration and AI integration
- Chat conversation management
- Task workflow execution
- Model Context Protocol (MCP) orchestration
- AI provider integration (AI Foundry, AWS Bedrock, GCP Vertex)
- User context and session handling
MCP Server Hub
Container Apps running MCP servers Model Context Protocol (MCP) servers act as standardized connectors to enterprise applications:Microsoft 365
- Outlook (Mail & Calendar)
- OneDrive (Files)
- SharePoint (Sites)
- Teams (Meetings & Messages)
Salesforce
- Read and write CRM data
- Query opportunities, leads, cases
- Update records
Jira
- Issue management
- Project queries
- Status updates
GitHub
- Repository access
- Code search
- Pull request queries
- NetSuite integration
- Microsoft Security (Defender)
- Web Scraping & Crawling
- Custom MCP servers (extensible)
Extend AVA to Any Enterprise Application
Leverage Your Existing SSO Infrastructure: AVA can integrate with virtually any application already configured as an Enterprise Application in your Microsoft Entra ID—if it uses OAuth or SAML for authentication.
- Use What You Already Have: Enterprise apps already in your Entra ID tenant can become AVA data sources
- OAuth/SAML Ready: If your app supports OAuth or SAML (most modern SaaS apps do), it can connect to AVA
- No Duplicate Auth: Leverages the SSO configuration you’ve already completed
- Delegated Permissions: Same identity-based security model as all AVA integrations
- HR Systems: Workday, BambooHR, ADP - access employee data, org charts, PTO balances
- Project Management: Monday.com, Asana, ClickUp - query tasks, projects, timelines
- Customer Support: Zendesk, Freshdesk, Intercom - access tickets, customer conversations
- Marketing Platforms: HubSpot, Marketo, Mailchimp - campaign data, analytics, contacts
- Finance Systems: QuickBooks, Xero, Bill.com - financial data, invoices, reports
- Custom Internal Tools: Any internal app with OAuth/SAML SSO configured in Entra ID
Data Layer
- PostgreSQL Database
- pgVector Extension
- Azure Blob Storage
Relational data storage
- User context and sessions
- Chat conversation history
- Task definitions and state
- Prompt library
- Activity logs
- Corpus metadata
AI Providers
AVA supports multiple AI providers for model flexibility:Azure AI Foundry
Primary provider
- GPT-4, GPT-4 Turbo
- GPT-3.5 Turbo
- o1, o3-mini models
- Embeddings (text-embedding-ada-002)
AWS Bedrock
Alternative provider
- Claude Sonnet
- Claude Opus
- Other Bedrock models
GCP Vertex AI
Alternative provider
- Gemini Pro
- PaLM models
- Task complexity
- Response speed requirements
- Cost considerations
- Context window size needs
Supporting Azure Resources
App Insights
Application monitoring, telemetry, and performance tracking
Key Vault
Secure storage for secrets, API keys, and connection strings
Managed Identities
Passwordless authentication between Azure services
How a Conversation Works
Let’s trace a typical user interaction:@ Mention Detection
Backend identifies @Salesforce mention and routes request to Salesforce MCP server
MCP Server Execution
Salesforce MCP server:
- Uses delegated user token
- Queries Salesforce with user’s permissions
- Returns only data user can access
AI Processing
Backend sends user question + Salesforce data to selected AI provider (e.g., GPT-4 via Azure AI Foundry)
How Knowledge Search Works
Knowledge Search uses Retrieval Augmented Generation (RAG):Document Ingestion
Services App Service:
- Connects to SharePoint using user’s delegated permissions
- Downloads documents user can access
- Chunks documents into manageable segments
Embedding Generation
- Each chunk is sent to embedding model (e.g., text-embedding-ada-002)
- Vector embeddings are generated
- Embeddings stored in PostgreSQL with pgVector
Auto-Sync (Optional)
If enabled, AVA periodically checks SharePoint for:
- New documents
- Modified documents
- Deleted documents Updates embeddings accordingly
Search Query
When user searches:
- Query is converted to vector embedding
- pgVector performs similarity search
- Top matching chunks are retrieved
How Tasks Work
Multi-step task execution:Step Execution
Backend processes each step sequentially:
- Evaluates step instructions
- Includes previous step results as context
- Can use @ mentions to pull live data
- SuperPrompt (if enabled) enhances AI guidance
Security Architecture
Authentication & Authorization
- ✅ Delegated Permissions: AVA uses SAML/OAuth to obtain delegated access
- ✅ User-Scoped Access: Every API call uses the authenticated user’s token
- ✅ No Privilege Escalation: AVA cannot access data the user cannot access
- ✅ Audit Trail: All actions logged with user identity
Data Security
Data Residency
Data Residency
- All data stays within your Azure tenant
- Processing happens in your tenant’s region
- No external SaaS data transfer
- You control data location and retention
Encryption
Encryption
- In Transit: TLS 1.3 for all communications
- At Rest: Azure-managed encryption for database and blob storage
- Secrets: Stored in Azure Key Vault
Network Security
Network Security
- Container Apps in isolated virtual network
- Managed identities for service-to-service auth
- No hard-coded credentials
- Azure Private Link support (optional)
Deployment Model
AVA is deployed as a single-tenant, private deployment for each customer:Your Azure Tenant
- Deployed entirely within your subscription
- You control all Azure resources
- No shared infrastructure
- Complete data isolation
Enterprise Application
- Registered in your Entra ID
- Uses your identity provider
- Integrates with your policies
- Respects your conditional access
- ✅ Data sovereignty: Your data, your tenant, your control
- ✅ Compliance-friendly: Easier to meet regulatory requirements
- ✅ Customizable: Can be tailored to your environment
- ✅ Secure: No multi-tenant security risks
Scalability & Performance
AVA is built to scale:- Azure Container Apps: Auto-scales based on demand
- PostgreSQL Flexible Server: Can scale vertically and add read replicas
- Blob Storage: Virtually unlimited storage capacity
- AI Providers: Load balanced across regions
- Chat responses: 2-10 seconds (depending on model and complexity)
- Knowledge Search: Sub-second vector search, 3-8 seconds total with AI generation
- Task execution: Varies by steps and data sources
- Concurrent users: Scales automatically with container app scaling
Monitoring & Observability
- Application Insights
- Logging
- Alerting
- Request/response telemetry
- Performance metrics
- Dependency tracking
- Custom events and metrics
- Failure analysis
Technical Stack Summary
| Layer | Technology |
|---|---|
| Frontend | React, TypeScript, Azure App Service |
| Backend | Python, FastAPI, Azure Container Apps |
| Database | PostgreSQL Flexible Server with pgVector |
| Storage | Azure Blob Storage |
| Identity | Microsoft Entra ID (SAML/OAuth) |
| Secrets | Azure Key Vault |
| Monitoring | Application Insights, Log Analytics |
| AI Models | Azure AI Foundry, AWS Bedrock, GCP Vertex |
| Integrations | Model Context Protocol (MCP) |
| Embedding | text-embedding-ada-002, pgvector |
